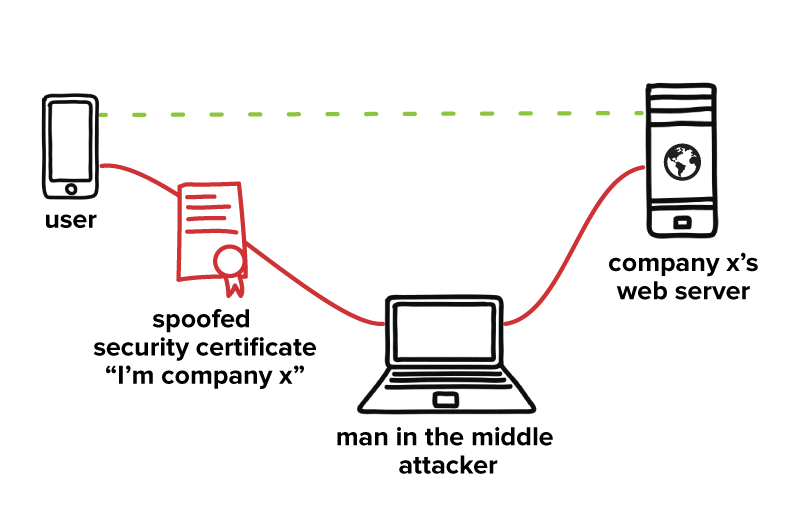
What is Mobile App Security? (Including 8 Application Security Tips) - Digital Brand Protection – FraudWatch

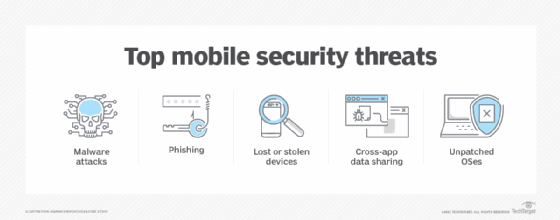
Keep Your Mobile Devices Secure - Information Security Office - Computing Services - Carnegie Mellon University
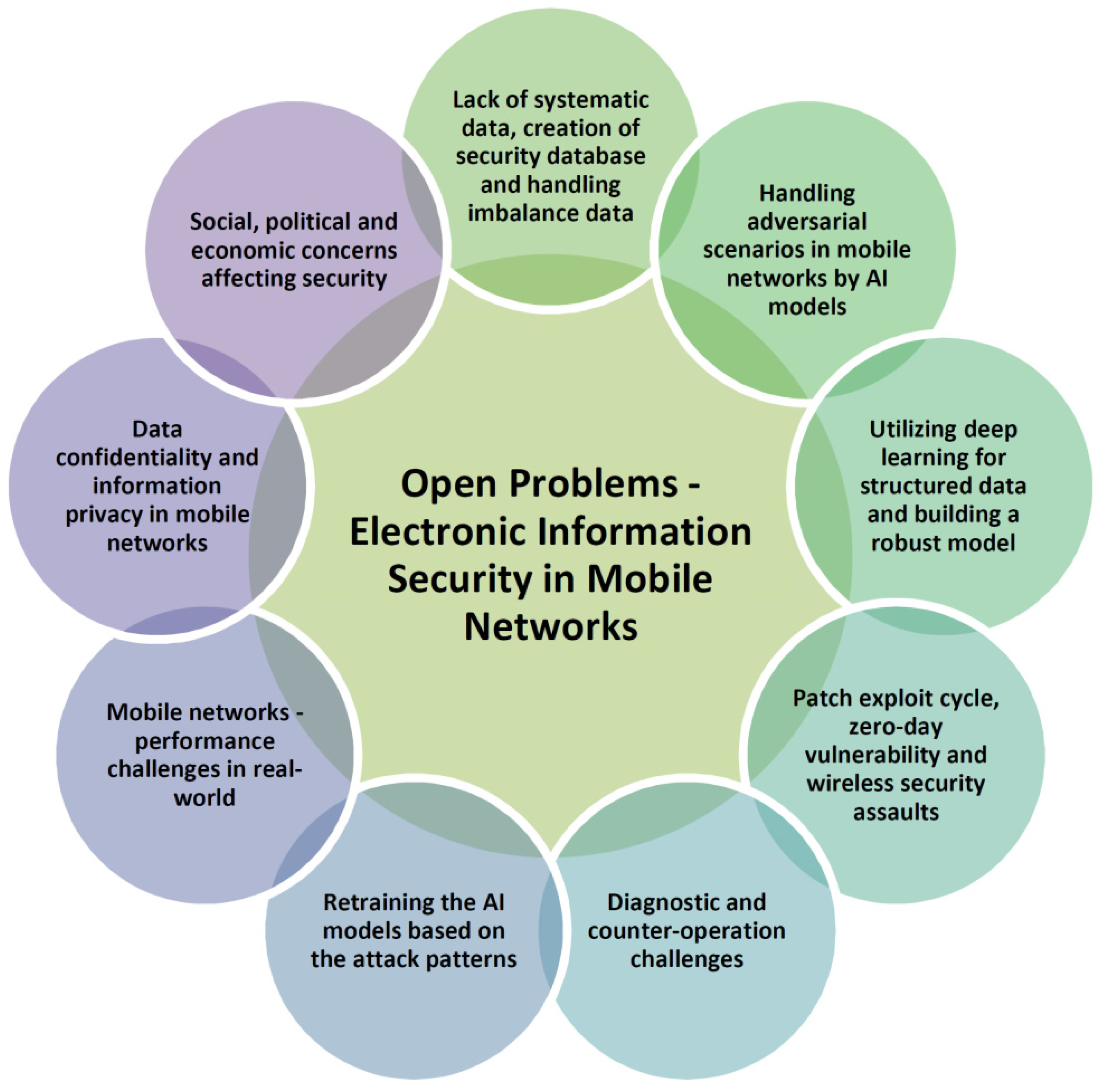
Sensors | Free Full-Text | A Systematic Review on Machine Learning and Deep Learning Models for Electronic Information Security in Mobile Networks

Smartphone and the security of your data #INFOGRAPHIC | Mobile data, Mobile security, Online security

Security Tip (ST19-003) Privacy and Mobile Device Apps – BGD e-GOV CIRT | Bangladesh e-Government Computer Incident Response Team