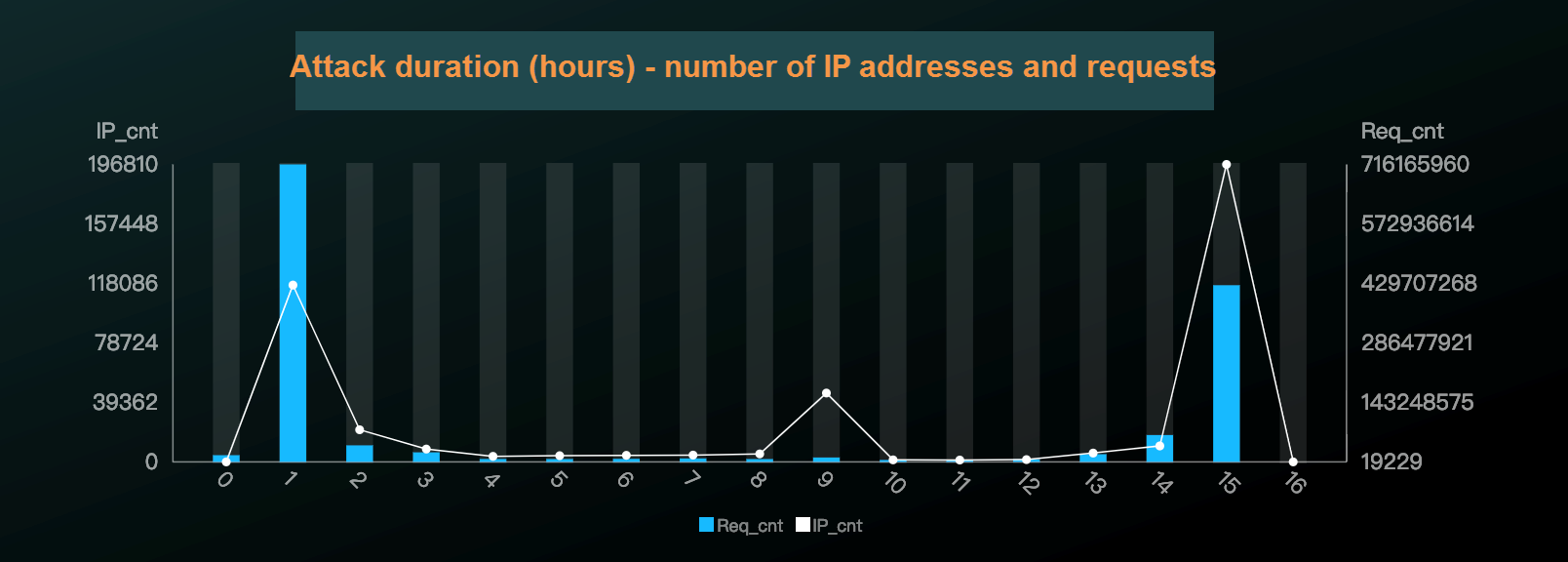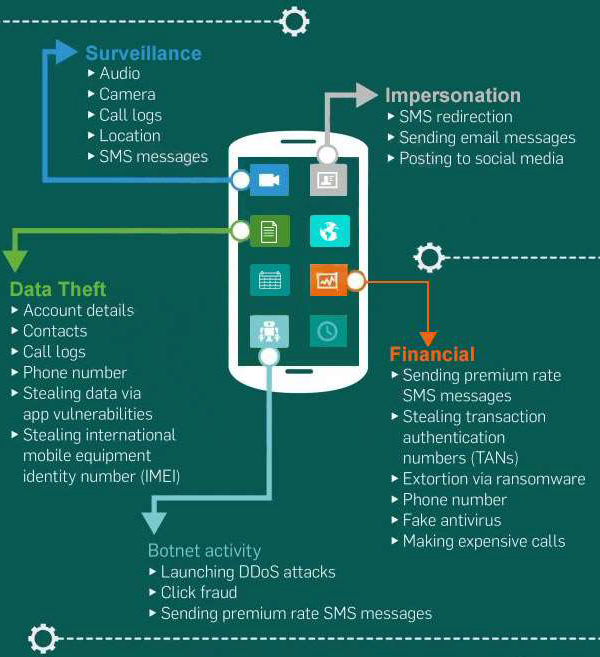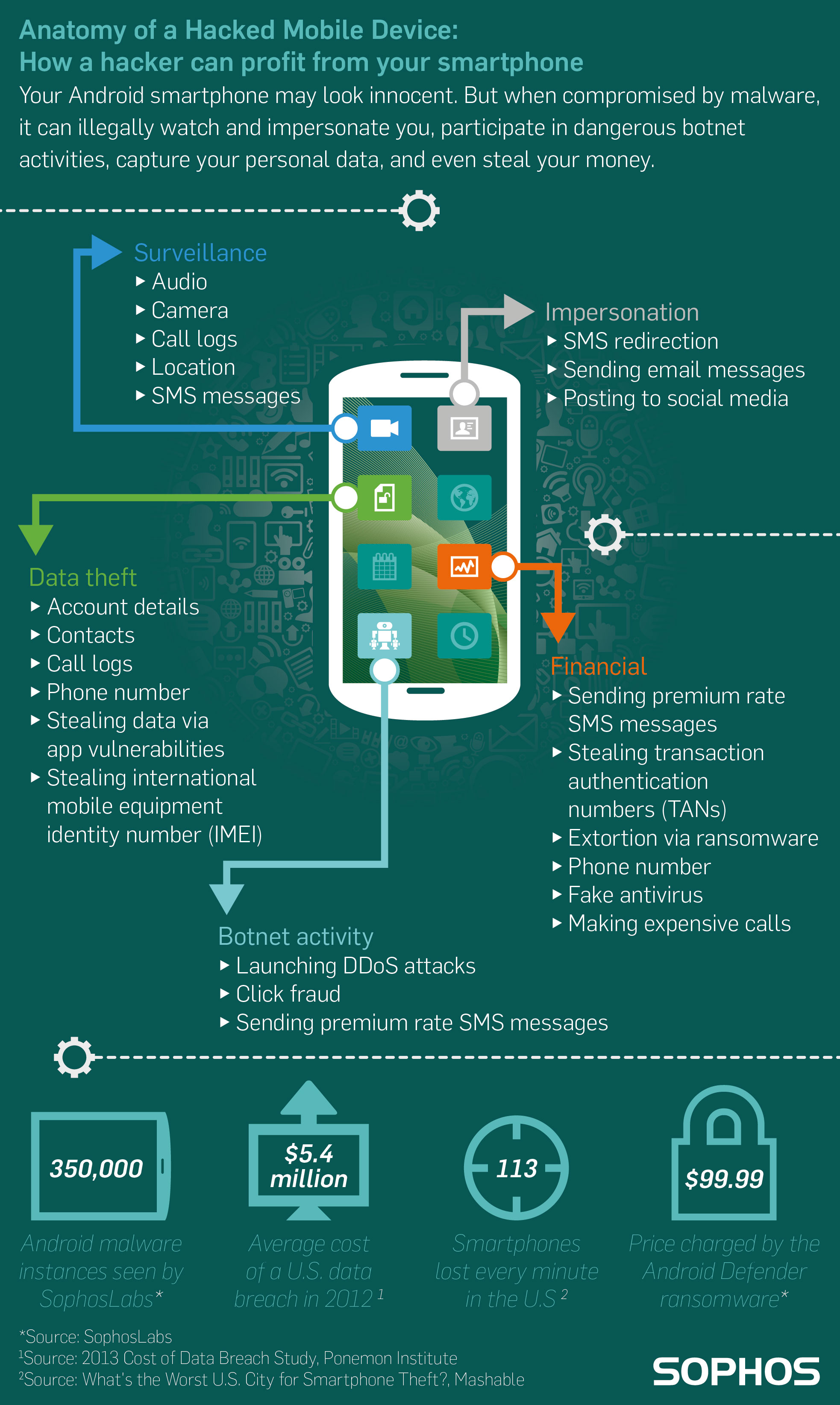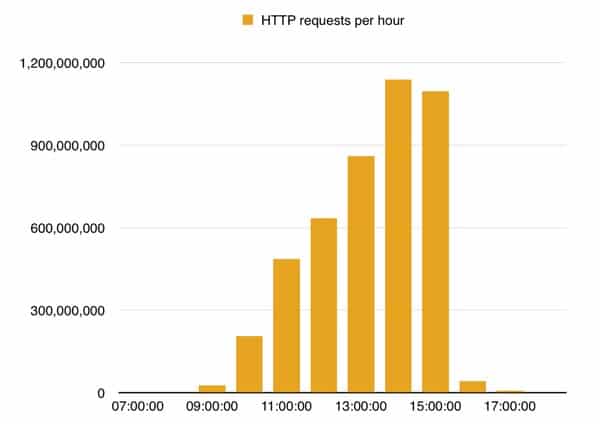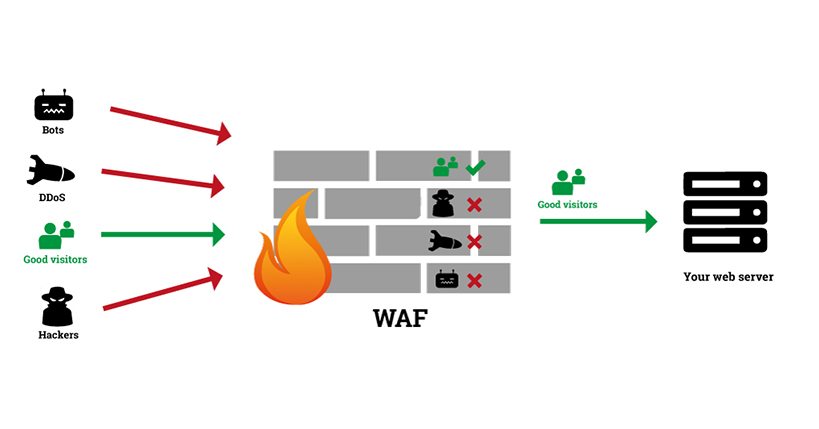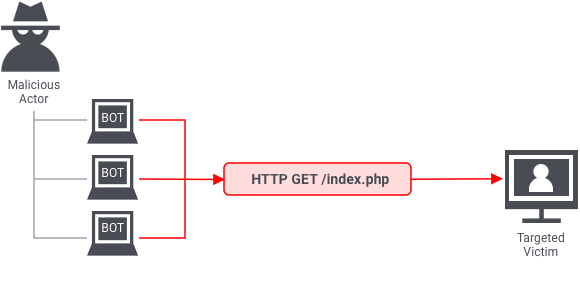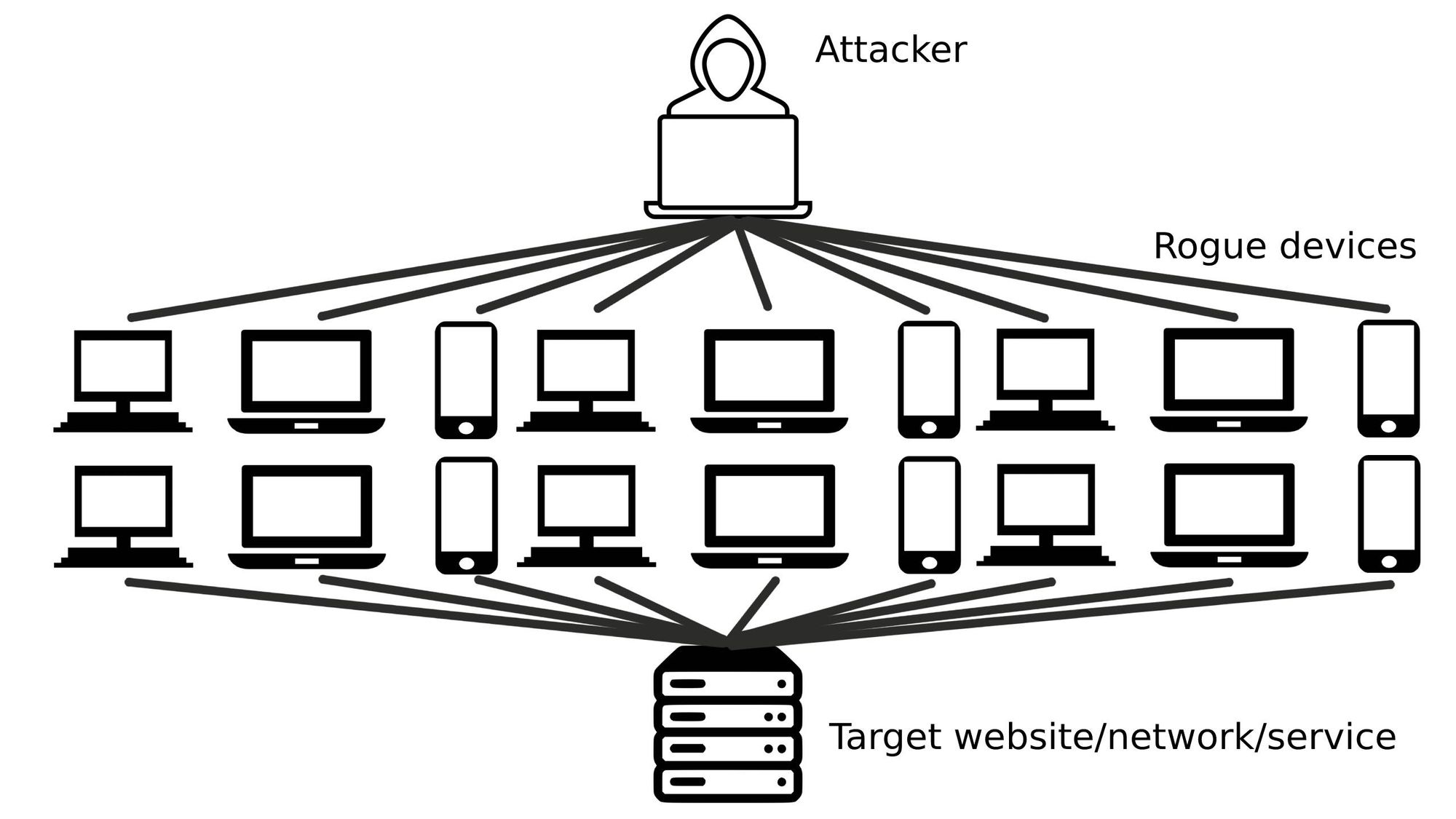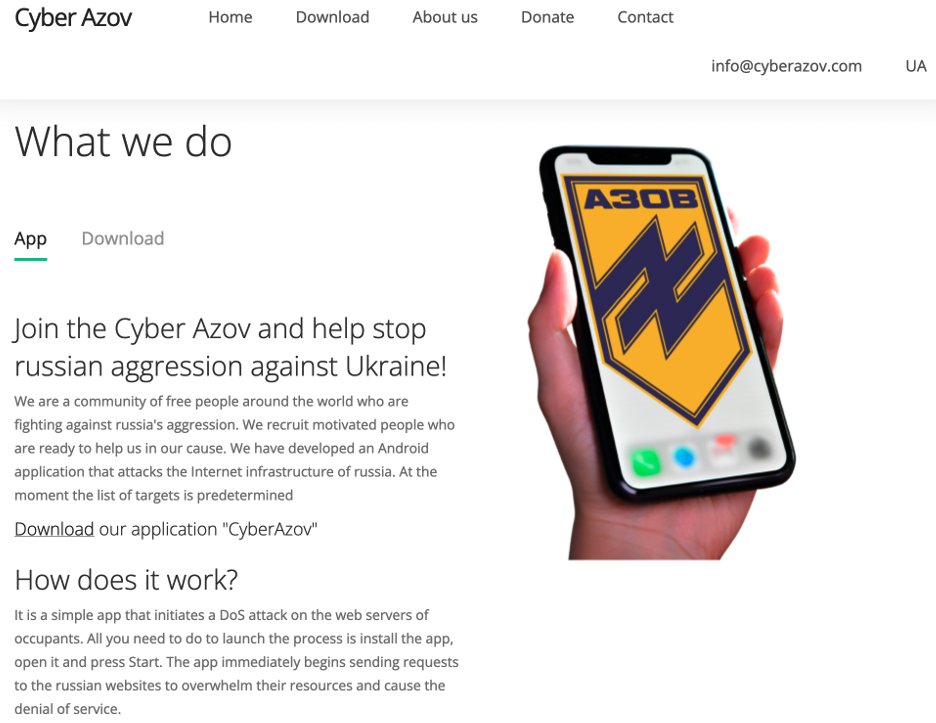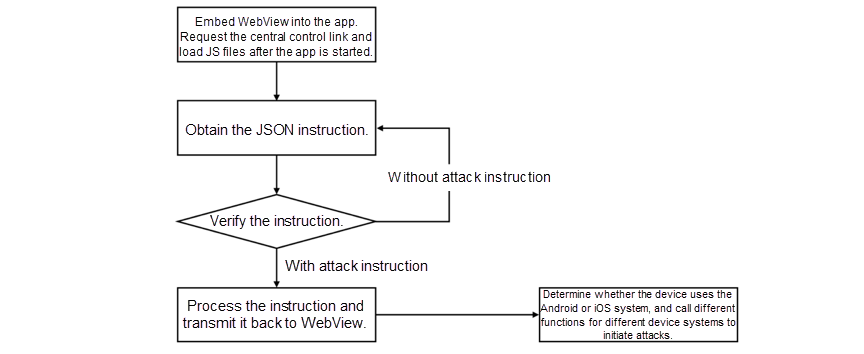
A New Trend of DDoS Attacks: Mobile Devices Are Becoming a New Generation of Botnets - Alibaba Cloud Community

Amazon.com: Galaxy S10 DDoS Attack - Denial Of Service - Hacker / Security Expert Case : Cell Phones & Accessories

DDoS attack resisting authentication protocol for mobile based online social network applications - ScienceDirect

Cloudflare claims pro-Russian hacktivist groups launched DDoS attacks on Australian organizations | Digital Watch Observatory